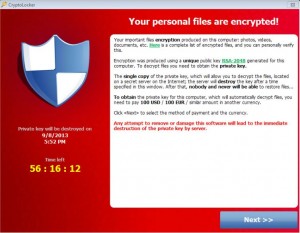
Over the past month or so, Recovery Force has been getting a lot of calls from clients who are abruptly prompted with a message saying that their data is now encrypted (which it is) and a request for payment of $300 for the decryption of their files.
What is it?
The best description of this threat is found on Trend Micro’s website. “CryptoLocker is the latest ransomware version that surfaced in 2013. It blocks access to the infected system and encrypts certain files.”
How can it be prevented?
Some things that we suggest are as follows:
- Make sure you have an up-to-date anti-virus program running in the background. It would be well advised to check the website of your particular anti-virus website to ensure that their latest definitions are able to detect and prevent this threat from gaining access to your system.
- Install a program that is specifically written to monitor and detect this threat. One such program we recommend was written by FoolishIT and can be found on their site here.
- One of the best ways to avoid ransomware and other threats is to avoid opening unverified email attachments and websites.
- As you can never be 100% sure that something won’t get through, you should make sure you have a solid backup routine in place. As this particular threat encrypts all data files connected to your system, either by network, USB or Firewire, it is good to have a backup copy that isn’t always connected to your systems.
What happens if already infected?
Unfortunately, there is no way for the data to be decrypted so you may have no choice but to pay the ransom. That said, Recovery Force might be able to find non-encrypted copies of your files on your hard drive. So, give us a call at 866-750-3169 if you’d like to find out if we are able to help.